Aug 5, 2021
LANCK Telecom FMS – Protection from PBX Hacking

LANCK Telecom is celebrating its 20 year anniversary. And we have a gift for our current and future partners:
Our innovative FMS with full functionality, for FREE!
Our FMS is already in use by nearly 100 enterprises, transit carriers, and mobile & fixed line operators. The system protects them against different forms of International Revenue Share Fraud (IRSF) and calls to Premium Rate Services (PRS) including:
- Unauthorized access fraud (PBX hacking, IP-PBX hacking, etc.);
- Conference call fraud;
- Roaming fraud;
- Wangiri and Wangiri callbacks;
- Enterprise callbacks fraud (Wangiri 2.0),
And many other types of nuisance calls such as robocalls, call bombing and silent calls for telemarketing or scamming purposes.
In a previous article we examined a novel fraud type – Wangiri 2.0. That article demonstrates our experience fighting a more well-known, but significantly risky fraud type – PBX hacking.
A PBX (private branch exchange) is a private telephone network within a company that connects the business to an external network of an operator.
Nowadays, PBXs (both IP or circuit-based) are considered an easy target for fraudsters because users are often unaware of the threat that PBX hacking poses and fail to implement even basic fraud protection.
For example, the PBX users don’t change the default passwords provided by switch vendors that are easily available online and in user manuals.
PBX hacking is a huge fraud risk for enterprises & telecoms and leads to enormous revenue losses.
According to the Communications Fraud Control Association (CFCA), in 2019 PBX hacking was the #1 telecom fraud method, causing a global fraud loss of $3.64 billion USD.
There exist two main fraud scenarios for PBX hacking:
- Pumping generated traffic through the victim PBX
- Pumping natural traffic through the victim PBX
It’s important to notice that although the second scenario is less popular with fraudsters, PBX hacking with natural traffic isn’t so easy to detect.
Here, we consider the fraud scheme from the first (most popular) scenario.
Fraud scheme:
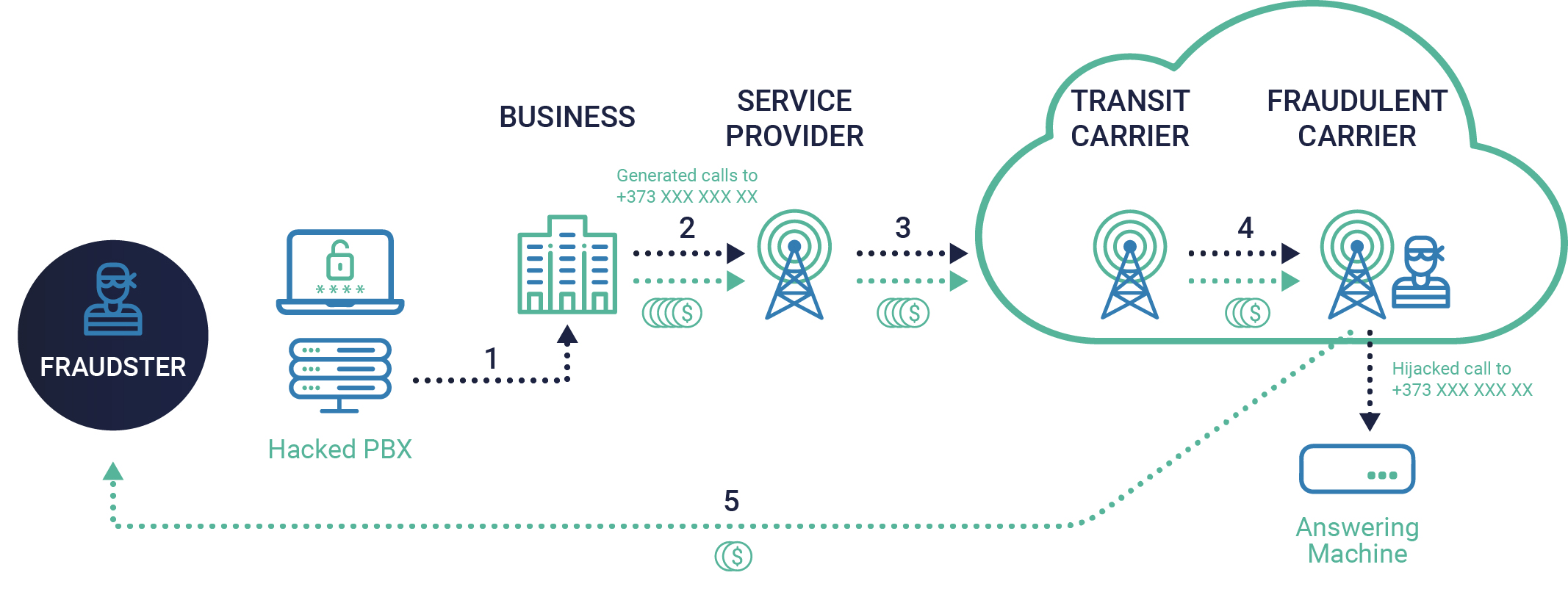
Description:
- A fraudster hacks a PBX (or IP PBX) of a business.
- Using that PBX, the fraudster generates telephone calls to +373 XXX XXX XX and passes them through a service provider.
- The service provider sends this traffic through its transit carrier.
- In the chain of transit carriers, the traffic passes to a fraudulent carrier that hijacks these calls connecting them to an answering machine (without passing the calls to the real subscribers) and, thus, bills them.
- After the fraud attack finishes, the business originates a payment flow (i.e. by the time the fraud is discovered the evidence of PBX hacking has been destroyed by natural log cycles to save storage space; or the fraud is never discovered at all), that reaches the fraudulent carrier, who shares the profits with the initial fraudster.
How fraudsters make attacks more difficult to detect:
- Disguises of statistical patterns of traffic (to look like natural traffic).
- Sustained simultaneous calls: if an antifraud system is not signaling-based (i.e. cannot monitor active calls and break them), then the presence of an attack can be detected only after the fraudulent calls have finished.
- Dynamic hijacking of calls (i.e. calls are hijacked for a very short time period, making it impossible to find the presence of a hijack via test calls).
Outcomes of fraud attacks:
As most antifraud systems are CDR-based, cannot break active calls, and have poor performance with traffic disguised with statistical patterns, attacks can last for hours and may not be detected at all. This can lead to enormous financial losses for a business (up to hundreds of thousands of USD per attack).
Even if a company successfully stops a payment flow, it faces reputational losses, as well as losses related to dispute process arrangement (it also negatively affects every carrier in the chain).
With LANCK Telecom, these threats are prevented. Let’s take a look.
LANCK Telecom FMS:
- Handles every scenario of PBX hacking fraud (including pumping of natural traffic through the victim PBX).
- Detects and stops PBX hacking attacks quickly in real-time (as FMS is a signaling-based system).
- Effectively identifies PBX hacking attacks even if fraudsters try to disguise statistical patterns of traffic and make the attacks difficult to detect (the points mentioned above).
Reach out to us if you want to protect your business from PBX hacking and all other fraud types.
Don’t miss your chance to get our FMS for free: contact fms@lancktele.com.
In our next article, we demonstrate how we protect against Wangiri fraud. Follow us on social media to not miss any news!







