Jun 30, 2021
LANCK Telecom FMS. Protection from Wangiri 2.0

Our FMS has a whole range of key advantages that make the system unique on the market. You can find the information about it in our previous article.
More than 80 enterprises, transit carriers, and mobile & fixed line operators that use our FMS, are protected from different forms of International Revenue Share Fraud (IRSF) and calls to Premium Rate Services (PRS):
- Unauthorized access fraud (PBX hacking, IP-PBX hacking, etc.);
- Conference call fraud;
- Roaming fraud;
- Wangiri and Wangiri callbacks;
- Enterprise callbacks fraud (Wangiri 2.0),
and different types of nuisance calls including robocalls, call bombing, and silent calls with telemarketing or scam purposes.
In this article we would like to share with you our experience in fighting a novel fraud type – Wangiri 2.0. First of all, this type of fraud affects enterprises: online-shops, social networks, audio/video chats, etc. But it also affects operators in the traffic supply chain.
LANCK Telecom was the first on the market to draw attention to this type of fraud in late 2018. Since then, our FMS identified and stopped a lot of Wangiri 2.0 attacks. According to our data, the number of Wangiri 2.0 attacks is gradually rising: In Q2 2021 the number of attacks increased by 20% compared to Q1 2021. The main reason for it is that many enterprises (as well as operators) do not even know about the existence of Wangiri 2.0.
Let’s look at the general fraud scheme of Wangiri 2.0.
Fraud scheme:
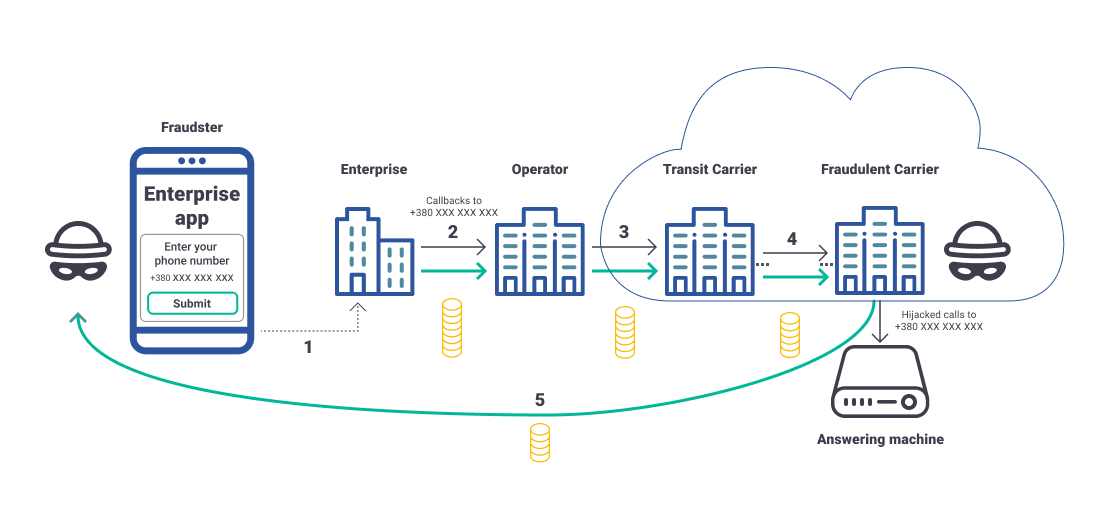
Description:
- A fraudster uses different phone numbers of real subscribers to request one-time passwords (PIN-codes) from an enterprise.
- The enterprise automatically calls back to these numbers via an operator (each call contains a voice record with password).
- The operator sends this traffic through its transit carrier.
- In the chain of transit carriers, the traffic passes to a fraudulent carrier that hijacks these calls connecting them to answering machine (without passing the calls to real subscribers) and thus bills them.
- After the fraud attack finishes, the unsuspecting enterprise originates a payment flow that reaches the fraudulent carrier, who shares the money with the initial fraudster.
How fraudsters make the attacks more difficult to detect:
- Mix of natural and fraudulent traffic.
- Constant switching between lots of different hijacked B-ranges.
- Dynamic hijacking of calls (i.e., calls are being hijacked during a very short time period – that is why it is impossible to find the presence of a hijack via test calls).
Outcomes of fraud attacks:
As most antifraud systems do not identify Wangiri 2.0 fraud, the attacks can last for hours, or even days. It leads to huge amounts of financial losses (up to many thousands of USD per attack) for an enterprise, because it pays for all the hijacked calls, which have zero-conversion for its business.
LANCK Telecom FMS:
- Handles all the scenarios of Wangiri 2.0 fraud.
- Detects and stops Wangiri 2.0 attacks very quickly in real-time (as FMS is a signaling-based system).
- Effectively identifies Wangiri 2.0 attacks even if fraudsters try to disguise them and make them difficult to detect (the points mentioned above).
Reach out to us if you want to be protected from Wangiri 2.0 as well as other fraud types. You can contact us at fms@lancktele.com.
In the next articles we will show our experience in protection from other IRSF scenarios. Follow us on social media and don’t miss any news!






